 My first computer book was “Basic for Children with Arturo”. It was 1989, the book was in Russian, and I was 10…
My first computer book was “Basic for Children with Arturo”. It was 1989, the book was in Russian, and I was 10…
Back then, in USSR, to own a 8086 compatible PC was somewhat mystical, and therefore people, who knew a thing or two about microelectronics, were putting together Speccy(s) (ZX Spectrums), which were based on Zilog Z80 8-bit microprocessor and ran at 3.5 MHz.
The official ZX-Spectrum that was sold by “Sinclair Research Ltd” at that time was a bit pricey for middle class families, and therefore many cities across Europe and USSR started to come up with their own “clones“. There were over 50(!) semi-official clones that came out by the end of 1980s, beginning of 1990s. But to cut cost even further, people who knew “how to solder” created hybrids of the clones at home, which came out to be very cheap.
The process to build ZX-Spectrum’s clone’s hybrid was “a bit” involved, and included many days/weeks of hacking poor, incomplete electrical circuit documentation and sleepless nights of manual calibration of the hardware. The one had to “get” a ZX-Spectrum full circuit schema:
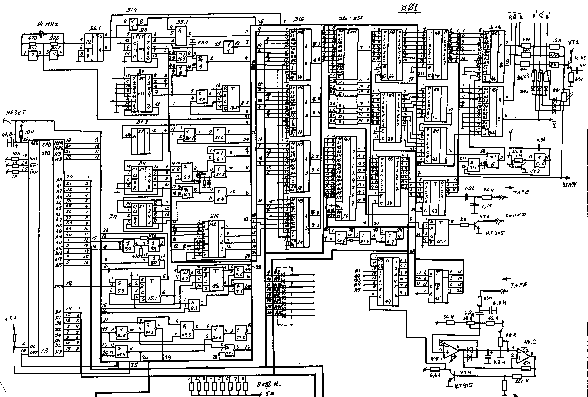
Study it, change it to fit the budget. Go to several flea markets to first find a CPU, which was a quite rare find:

plus many more components: an empty electrical board, all other chip, transistors, capacitors, resistors, etc…
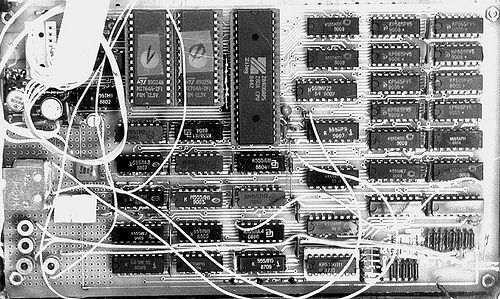
After some time and a combination of new ideas, documentation, hardware and labour, the one ended up with something like this:
ZX-Spectrum keyboard had an interesting feature – pretty much every key, depending on the combination of special keys used, could represent 3-4, sometimes even 5 different things (commands/letters/symbols/special characters/etc). This made it much smaller (“compacter”) than for example PC keyboards:

And due to its small size, it most of the time served as a ZX-Spectrum case, and fit it the Speccy’s “motherboard”:

There were also some alternatives, and some people used “an extended” keyboards, but “a single key multi-purpose” pattern was still there. Here is a snippet of the Russian ZX-Spectrum keyboard, for example:

which is “a bit extended” – has a separate cursor, and some other keys. But take a look at the individual keys – due to the additional Cyrillic letters, “an average key” is now used to represent even more (+1) values.
At this point, when most of the work with oscillograph was behind, the only true way to see if the creation works was to see it with your own eyes. The word “monitor” in a sense of a “computer monitor” was not a widely used due to its price mostly, therefore most of ZX-Spectrum people used old black and white (at first) TVs. Speccy (well it’s clone’s hybrid at least) was designed in a way that it could be pugged into a regular TV Antena’s jack:
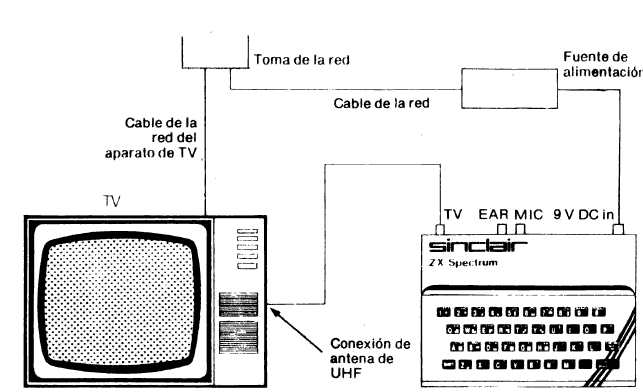
And due to the fact that family is usually more than one person, the main TV often was not used, and people used old TVs as a Speccy “monitor” instead:

The whole process above was about 50% of the job – yea, just 50%. The other half was split on two. First quarter was spent in calibrating hundreds of little circuits, in order to get a sacred “© 1982 Sinclair Research Ltd” message at the bottom of TV (monitor):
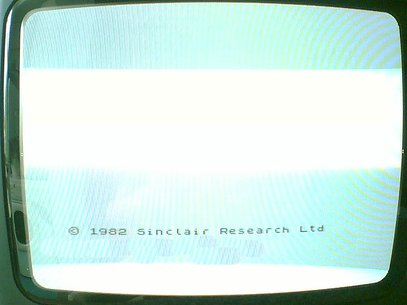
This message brought lots and lots of joy into families once it appeared on the screen. It meant a lot – CPU was working (so that guy on the flea market who sold it to you was ok.. sigh…). ROM was working (so that guy on the flea mark…). CPU and ROM were calibrated to work together, along with RAM and some other parts.
Usually the one plugged in Speccy to TV with no RAM/ROM/CPU at first, and calibrated all the circuits to reach a documented pattern on TV (for example small squares). After that was achieved, RAM/ROM and CPU were inserted one after the other by the same technique – each had to produce a certain visual pattern. So if all the parts were inserted and the message “© 1982 Sinclair Research Ltd” appeared, job was 75% done.
The last quarter was usually spent to tune all the parts to work as designed. Most of the time Speccy would restart in 3-4 minutes of use, just because something was “out of it”. To find that “something” was an art on its own. There was no Internet, no books or literature on this – it was pure work of art!
Fortunately my father is such an artist, and by the time I was 10, I got one of those Speccy beasts that my dad and I put together. The only problem though was that although it was designed to have 64Kb of RAM, it only had 16Kb. Well, 7 months later we solder more capacitors around 4Kb RAM memory chips, and that fixed it, but for 7 months I could not really play any games, because most of them required 64Kb to be there. Hence, the “Basic for Children with Arturo” book did not get a chance to get too dusty…
Where ZX-Spectrum shined the most is of course boot time – there was none :) Well, everything was in a ROM chip, including Sinclair Basic.
So having spent about 4-5 months to build Speccy, I was out of luck, and could not use it. Well, that is how I saw it for the first one or two weeks. But then…. I pressed a “p” key, which by default was a Basic “print” command, and then…. I typed what was on my mind: “I want to play!”, and to my astonishment Speccy “said“: “I want to play!”.
It is probably hard to surprise anybody right now by the fact that computer prints something on the screen, when you ask him/her to, but for me, being 10, and haven’t seen anything cooler than that, it was the biggest technical discovery of all times. I picked up my Basic book, and started to type, and type, and type, and then…. type a little more. That is how I started. That, in programming sense, makes me a “Speccy Child”.
A program in Basic in Speccy looked something like this:
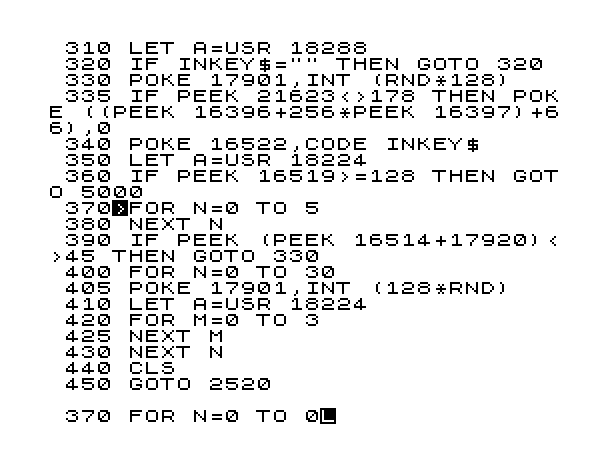
where every line had to have a number, and the usual increment was 10. Quickly my favourite commands became “peek”, “poke” and “randomize” which worked directly with the memory (absolute addresses). And although I felt like a memory King, something was missing. I figured out what it was after I bought a system program that exposed me to something much more powerful than Basic – it was 8-bit Assembly language, the language that Zilog Z80 talked natively. Therefore me together with Z80, could control pretty much everything in the Speccy kingdom. That was awesome!
Here is an example on how you’d print a line of text to the screen in Speccy’s native language:
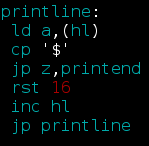
Cool – huh!? Another thing that was very useful at the beginning of my Assembly journey, was a documented character table ( like an “ASCII” ):
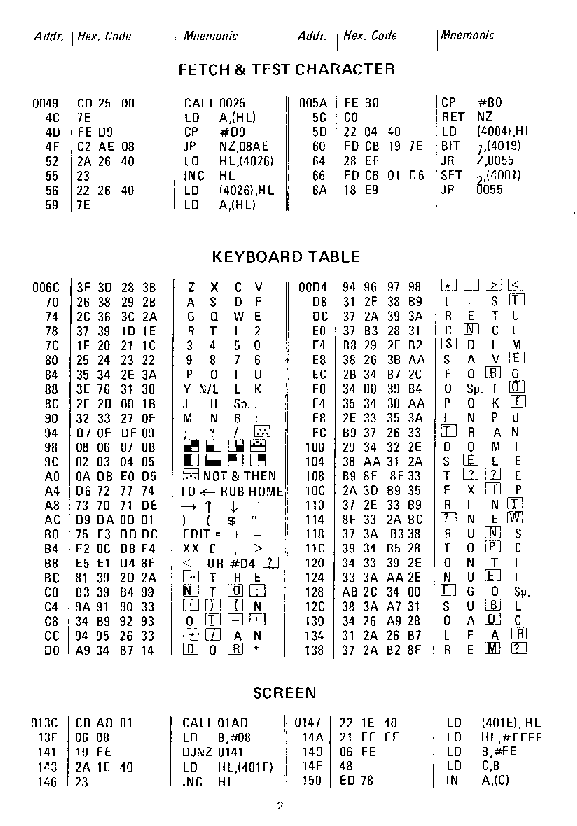
The only problem was that in order to work in Assembly, or in any other language, or with any other system program – it needed to be loaded since it was not in RAM/ROM – and that took time. No, really took time. It needed to be loaded from a tape – a regular cassette that is used in a tape recorder. In fact these very tape recorders were used to load all these neat programs in:

But not only it did take time to load, it was a constant pain to tune the head of the tape recorder for each tape bought on the flea market, since nobody followed the recording standards. A lot of times, you would have to sit and hold a screwdriver against the recorder’s head for 3-5, even 10 minutes, depending on how big the program was.
Here is what the screen looked like when the program was loading from tape into RAM. You can see the zebra looking lines, they were the moving loading indicator:

But time went, flea markets grew along with demand, and we upgraded to the real “RGB deal”. It was done by soldering an external controller (kind of like modern video cards, but not really) that had an RGB jack:
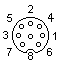
Although it had 9 pins, only 5 were used: Red / Green / Blue / Sync / Ground. But we did not stop on this. Soldered another external controller, but this time for a disk drive! Oh yea – that was a huuuge deal. Looking at programs to load for seconds (well in rear occasions minutes) from these beautiful 5 inch disks!
Since we had a disk drive, Speccy needed to catch up with us, and the disk controller brought another cool thing, which was TR-DOS, where, of course, DOS stands for Disk Operating System. That is how pretty it looked:

Did you notice some colour? Good catch :) So now it was possible to actually browse the disk, and start programs with a button click. There were tons of system utilities with different browsers that you could start at the start up time (sort of like in MBS, but not).
Right after TR-DOS, I felt like I need more. I need more.. I need more.. RAM! And we soldered another level of RAM on top of 64Kb chips. So now my Speccy was equipped with 128Kb of RAM, which could free up some ROM real estate, which enabled ROM to fit a little menu on startup:

At this point not only I could swim in the Assembly language ocean, but also play games, and use various utilities!
First let’s look at Photoshop:
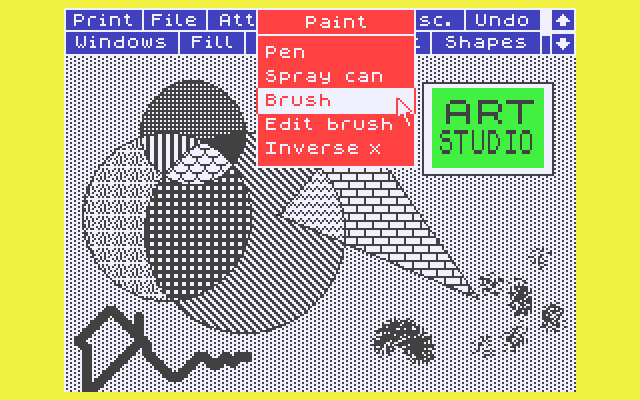
well, maybe not the Photoshop you’re used to see right now, but Art Studio rocked! I was drawing away for hours!
Now, how about CuBase/ProTools:
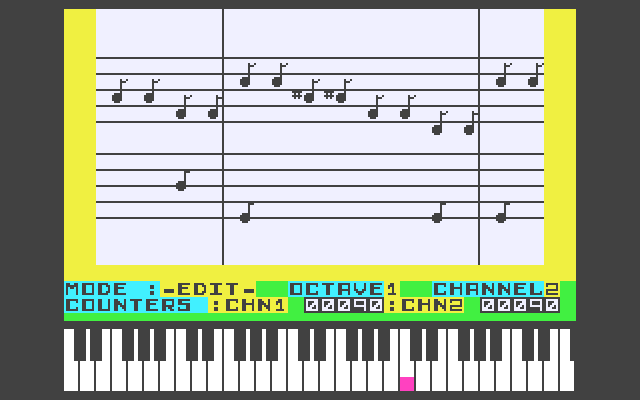
well, maybe not exactly the latest CuBase, but I wrote lots of tunes in Wham. Some tunes I actually recorded along with playing a real guitar – it was cool!
As to games, my favourite control was my keyboard, but for many friends that came to play, I bought a joystick:

Now we could play multiplayer games like:
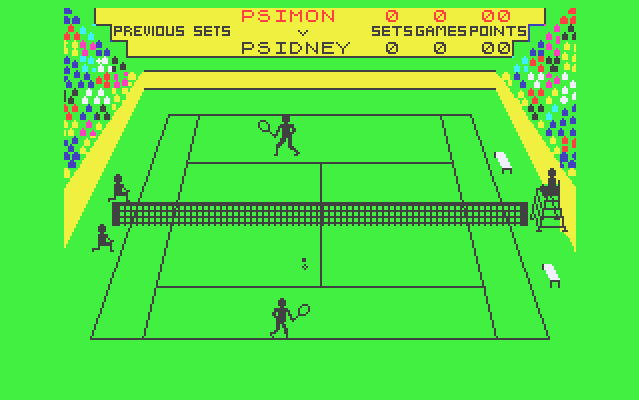
Match Point (Tennis) or:
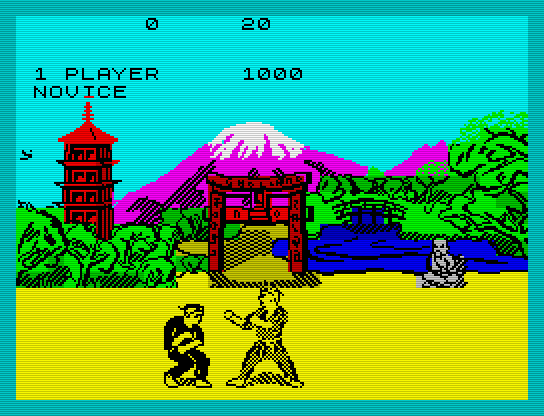
Fist (Karate) game. Or even:

Tetris2 – which was a bit different from the regular Tetris in a way it gave different patterns and challenges on different levels, and was also a multiplayer game, which was of course cool.
There were tons of other games, but two I still remember are Robocop:
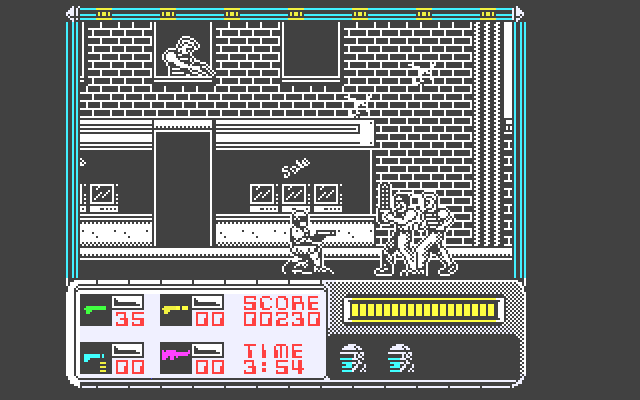
and Bomb Jack:
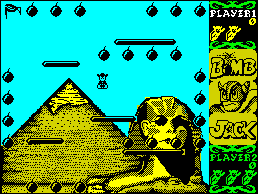
I could play long long time in Bomb Jack, not longer than I spent writing my own little games in Assembly language of course, but still – it was good amount of Bomb Jack time.
All the above was of course some time ago… 25, or even soon 30 years. Everything is a bit different now. Speccy lives somewhere in museum behind the glass:

But I remember him/her – those were times of big discoveries for me!
Like probably right now for some other 10 year old kid who just accidentally pressed a “p” button, and discovered….. time traveling…
Good luck to you kid!

 A standard “home setup” for the wireless router now days consists of just hosting one Service Set IDentifier – or
A standard “home setup” for the wireless router now days consists of just hosting one Service Set IDentifier – or 





 I usually keep my blog technical and life oriented, however today, after the “$700 billion bailout deal” did not pass, and White House is cooking up a new deal, I think it is ultra important to convey the message of top US Economists from many US Universities that “This bailout is NOT the answer to the crisis!”.
I usually keep my blog technical and life oriented, however today, after the “$700 billion bailout deal” did not pass, and White House is cooking up a new deal, I think it is ultra important to convey the message of top US Economists from many US Universities that “This bailout is NOT the answer to the crisis!”.
